Ethical Hacking & Cyber Security with AI
Ethical hacking is the practice of intentionally breaking into computer systems, networks, and applications—with legal permission—to find and fix security weaknesses before malicious attackers exploit them. Ethical hackers use the same tactics as black-hat hackers, but to strengthen an organization’s defenses and build stronger cybersecurity walls.
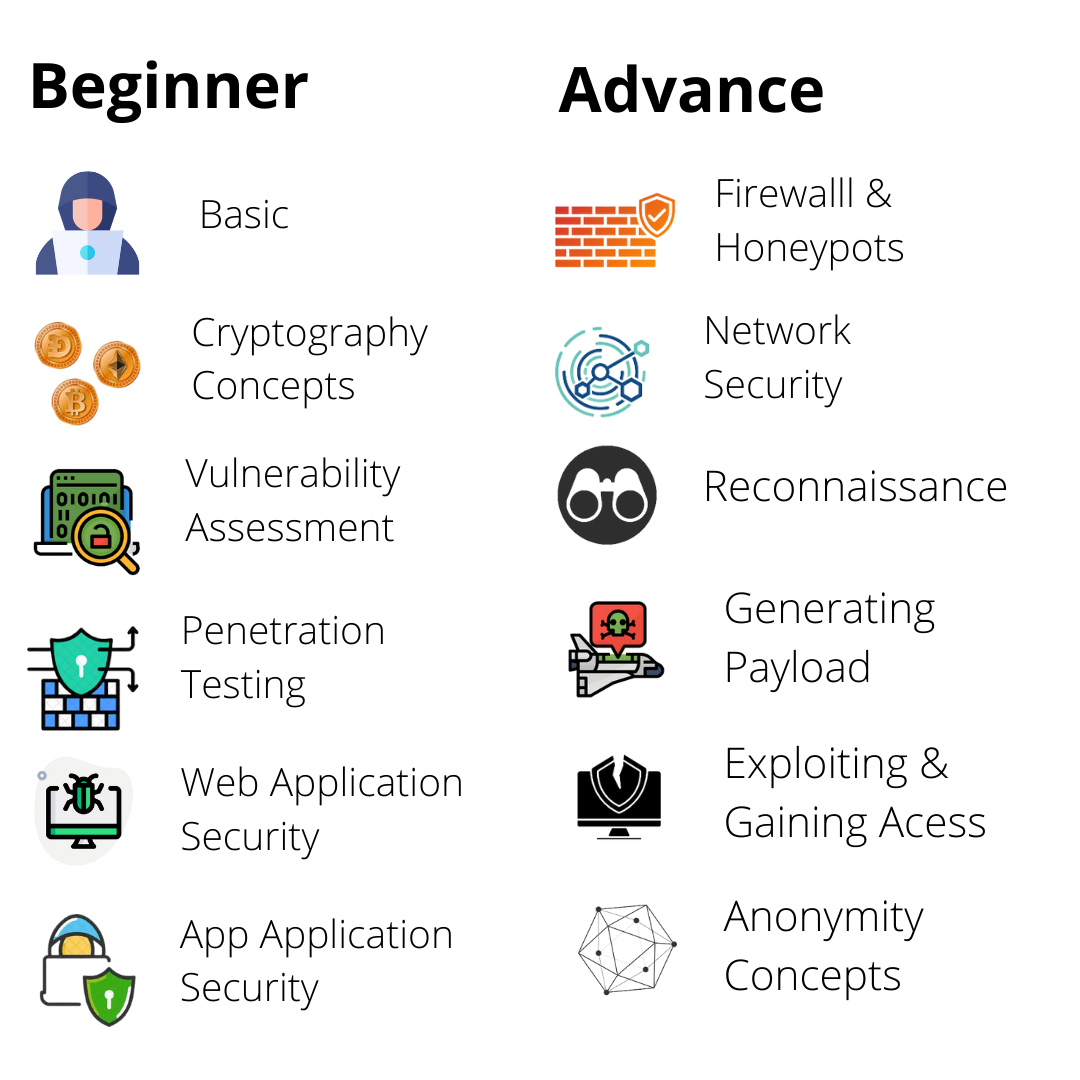
Key Components of Ethical Hacking
Penetration Testing Tools: Learn to simulate real cyber-attacks using tools such as Metasploit, Nmap, Wireshark, and Burp Suite to uncover vulnerabilities in systems and networks.
Programming Languages: Gain proficiency in Python, Java, and C/C++ to automate tasks, write scripts, and develop security tools.
Networking Fundamentals: Understand protocols, configurations, and network architecture to identify flaws and prevent unauthorized access.
AI & Automation in Security (Optional Module): Explore how modern cybersecurity leverages AI for threat detection, anomaly analysis, and automated incident response.
Why Choose Ethical Hacking?
High Demand for Cybersecurity Professionals: With cyber-attacks rising globally, companies need certified ethical hackers to protect sensitive data and critical infrastructure.
Legal & Ethical Practice: Apply hacking skills responsibly and lawfully to help organizations strengthen their defenses.
Continuous Learning & Growth: The cybersecurity landscape evolves rapidly, keeping your skills in demand and your career future-proof.
Ethical hacking offers a rewarding career path for those passionate about cybersecurity and technology. By helping organizations improve their security posture and defend against digital threats, ethical hackers play a critical role in safeguarding data, building trust, and protecting the digital world.
Key Highlights of our Course
What you'll learn in this course
Heuristic Academy provide you
- 6 Months Intense Training
- Offline E-Learning with Industrial Professionals
- Hands-On Experience on 10 Live Projects
- Interview Preparations with Mock Interviews
- Campus Activities (Project Competitions & Tech Events)
- Internship Certificate after Completion of Course
- 100% Job Placement Assistance
Choose the right Development course for you.
FAQ
The average salary of an Ethical Hacker or Cybersecurity professional can vary depending on factors such as experience, location, and skillset. Here's a general breakdown:
- Entry-Level (0–2 years): ₹3LPA to ₹6LPA
- Mid-Level (2–5 years): ₹5LPA to ₹12 LPA
- Sr-Level (5+ years): ₹12LPA to ₹15LPA or higher
Cybersecurity and ethical hacking are for people who love technology, security, and keeping digital assets safe. It's great for people who like to solve problems, stay up to date on new security threats, and protect themselves from online attacks.
While a specific degree isn't mandatory, a background in computer science, information technology, or related fields is beneficial. Paths to entry include:
1. Bachelor's Degree: Computer Science, Information Technology, Cybersecurity, or related fields.
2. Courses: Platforms like Heuristic Academy offer comprehensive courses in ethical hacking and cybersecurity, Which provide the Student with complete understanding of the Field.
3. Certifications: Pursuing certifications such as CEH (Certified Ethical Hacker), CompTIA Security+, or CISSP (Certified Information Systems Security Professional) can enhance skills and credibility.
4. Self-Study and Projects: Hands-on learning through experimentation, capture the flag (CTF) challenges, and participation in cybersecurity communities.
Many industries have jobs in ethical hacking and cybersecurity.
1. Security Analyst: Checking and keeping an eye on security systems to keep cyber threats at bay.
2. Penetration Tester: Using fake cyber attacks to find weaknesses in networks and systems.
3. Security Consultant: helping businesses with security best practices and putting them into action.
4. Incident Responder: Responding to and reducing the effects of security incidents, breaches, and threats.
5. Security Engineer: Making and putting in place security measures to keep cyber threats at bay.
6. Chief Information Security Officer (CISO): In charge of the organization's overall security strategy and posture.
7. Cybercrime investigator: looking into cybercrime cases and gathering proof for court cases.
8. Security Architect: Designing networks and systems that are safe so that people can't get in and data can't be stolen.
- Hands-On Live Projects & Lab Environment
- Internship & Course Completion Certificates
- Expert Mentors with Industry Security Experience
- Placement Assistance & Interview Prep
- Updated Curriculum with Latest Threats & Tools
- Flexible Learning Options (online/live / hybrid)
- Lifetime Alumni Community Access
- Free Career & Resume Guidance
- AI-Enhanced Security Tools & Automation
Ethical Hacking & Cyber Security with AI Certification & Internship
Become a Certified Ethical Hacking & Cyber Security with AI, perfect your skills and accelerate your career with Heuristic Academy to get your dream job.
At Heuristic Academy, we go beyond traditional training. Our ISO-certified Ethical Hacking & Cyber Security with AI course is designed to build strong skills and real-world expertise. As part of the program, you’ll work on live projects that reflect industry practices. Upon completion, you’ll receive both a Course Completion Certificate and an Internship Certificate, validating your hands-on experience. These credentials are highly valuable for boosting your resume, LinkedIn, and career profile, helping you stand out in today’s competitive job market.


Choose the right Development course for you.
Share the opportunity to learn and grow & get rewarded for it!
📢 Refer a Friend
📝 Fill out the form and share your unique referral link with friends, family, or anyone interested in upskilling.
🎁 They Get a Gift Voucher
🛍️ Your friend will receive an Amazon or Flipkart gift voucher when they enroll through your referral link.
🏆 You Get Rewarded
💸 If your friend enrolls in any of our courses, you’ll receive a special gift and a cash reward of up to ₹1000 — delivered 30 days after their course begins!